A crypto user lost $440,358 in USD Coin (USDC) on Ethereum after unknowingly approving a fraudulent “permit” signature that allowed an attacker to drain their wallet, as confirmed by Web3 security platform Scam Sniffer. The victim using the wallet address 0x67E8561Ba9d3f4CBe5fEd4C12c95b54f073a0605, approved a malicious transaction that granted an attacker full spending rights. Scam Sniffer spotted the funds being sent to two separate addresses labelled 0xbb4…666f682aF and 0x6a3aF6…d8F9a00B. Phishing attacker signs off on $440K USDC transfer from victim According to blockchain data from Etherscan, the attacker relied on a “permit” transaction, a type of signature that transfers tokens without requiring the owner to confirm them manually. Even if no money appears to move at the moment of signing, the attacker can later fill in the amount and cash it without further consent, which, in this case, $440,358 was filled. Once approved, the attacker invoked several “transferFrom” calls using the FiatTokenProxy contract, which handles USDC transactions. At around 10 AM UTC Monday, 22,000 USDC was sent to a “Fake Phishing” account, $66.06K to address 0xbb4…666f682aF, and $352.3K to 0x6a3aF6…d8F9a00B simultaneously. victim: 0x67E8561Ba9d3f4CBe5fEd4C12c95b54f073a0605 scammers: 0xbb4223Ef4cCe93fB40beb62178aBE9A666f682aF 0x6a3aF6Cb51D52F32D2A0A6716a8EFF99d8F9a00B https://t.co/GdyGP2iPYZ pic.twitter.com/IukksnpAl1 — Scam Sniffer | Web3 Anti-Scam (@realScamSniffer) December 8, 2025 Scam Sniffer also reported on another phishing incident on November 7, when another user lost $1.22 million in USDC and a PlaUSDT0 token just 30 minutes after signing fraudulent permit messages. The Web3 security firm’s November phishing report shows total losses reached $7.77 million, a jump of 1137% from October’s $3.28 million. Despite the surge in losses, the number of victims decreased by 42%, as November recorded 6,344 affected users, a 42% drop from the 10,935 victims logged in the previous month. Almost a week ago, some hackers used “address poisoning” to steal 1.1 million USDT on Ethereum. According to Ramiel Capital CIO Kyle Soska, the group monitored small outbound transfers from whale wallets and then used GPU-powered systems to generate near-identical look-alike addresses. “The attacker in this case sends a very small tether transaction to the victim on-chain so that the look-a-like address appears in the recent activity list of the victim’s web3 wallet. The victim then accidentally chooses this address to send the big money to,” Soska said, replying to an X user asking how the incident was even possible. Holiday shopping season flooded with impersonation scams The escalation in crypto-related phishing comes on the heels of an uptick in digital scams in the holiday shopping season. Darktrace, a cybersecurity firm tracking global consumer phishing trends, reported a 201% rise in scams of “impersonating” major US retailers during the week leading into Thanksgiving, compared to the same week in October. Emails spoofing Macy’s, Walmart, and Target rose by 54% in a single week, but Amazon was the most impersonated company overall, accounting for 80% of phishing attempts, more than digital consumer brands Apple, Alibaba, and Netflix. In early November alone, Kaspersky detected 146,535 spam emails referencing seasonal discounts, including 2,572 related to Singles’ Day campaigns. Many of these messages reused proven templates recycled from previous years, with scammers mimicking Amazon, Walmart, and Alibaba to advertise early-access sales that redirected users to fake checkout pages to steal credentials and execute malicious approvals. Data from Kaspersky Security Network (KSN) shows that between January and October, the company blocked 6,394,854 phishing attempts targeting online stores, banks, and payment systems. Nearly half of these attempts, 48.2%, specifically targeted online shoppers. Over the same period, Kaspersky identified more than 20 million attacks on gaming platforms, including 18.56 million abusing Discord, which the company says is a distribution point for malicious files disguised as gaming software. Entertainment platforms also saw intense targeting, with 801,148 Netflix-themed and 576,873 Spotify-related phishing attempts recorded in 2025. The company also documented 2,054,336 phishing attempts impersonating gaming platforms Steam, PlayStation, and Xbox. Moreover, Kaspersky recorded 20,188,897 attempted malware infections disguised as “common software,” with Discord accounting for the majority at 18,556,566 detections, more than 14 times higher than the incidents reported last year. Want your project in front of crypto’s top minds? Feature it in our next industry report, where data meets impact.
 Blue Origin and SpaceX compete for space AI
Blue Origin and SpaceX compete for space AI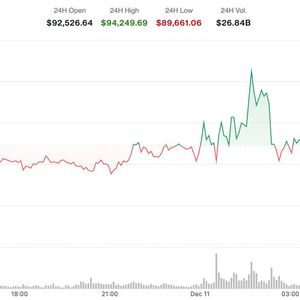 Why is Bitcoin Trading Lower Today?
Why is Bitcoin Trading Lower Today?






![[LIVE] Crypto News Today: Latest Updates for Dec. 11, 2025 – BTC Breaks Below $91K as Fed Signals Pause; DePIN, AI Lead Market Drop [LIVE] Crypto News Today: Latest Updates for Dec. 11, 2025 – BTC Breaks Below $91K as Fed Signals Pause; DePIN, AI Lead Market Drop](https://resources.cryptocompare.com/news/52/55627328.jpeg)


